MONI NetWave
Inside the Packet receiver and analyser is the patent MONI NetWave real-time packet propagation tracking.
This communicates with other nodes via your OOB management network.
NetWave is a multipoint analysis which tracks packets across a network.
It uses multiple MONI nodes to follow unicast, multicast and broadcast packets as they are sent/received.
It works by creating a signature (hash value) for packets as they pass through nodes and tracks the signature in other nodes.
This works for both encrypted and unencrypted traffic alike as it does not use the packet data to track.
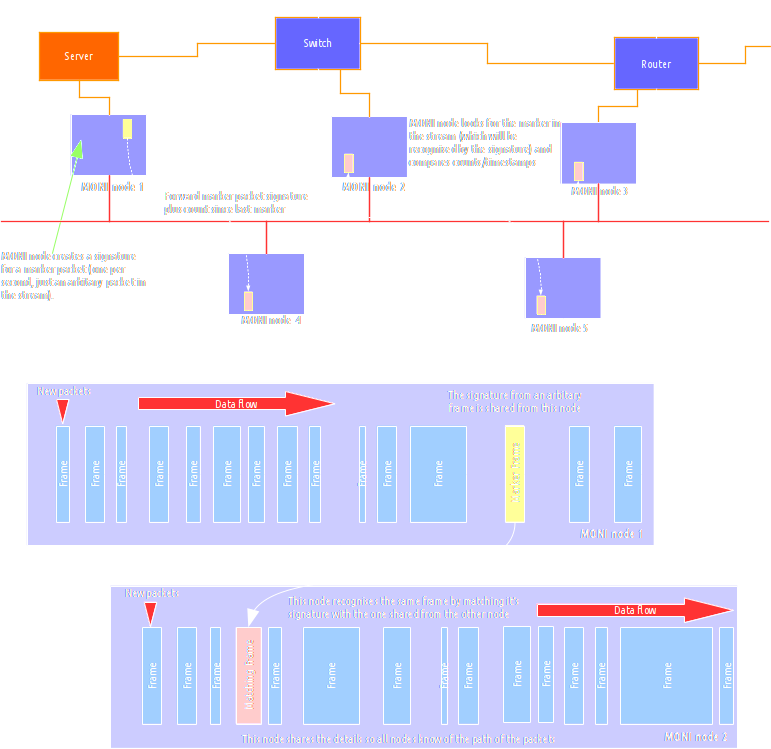
MONI NetWave also tracks packets through all firewalls since it tracks the data payloads not the headers.
This patent completely agnostic method can show any unexpected traffic patterns so you can really see the security holes.
You can see this shot of a real customer:
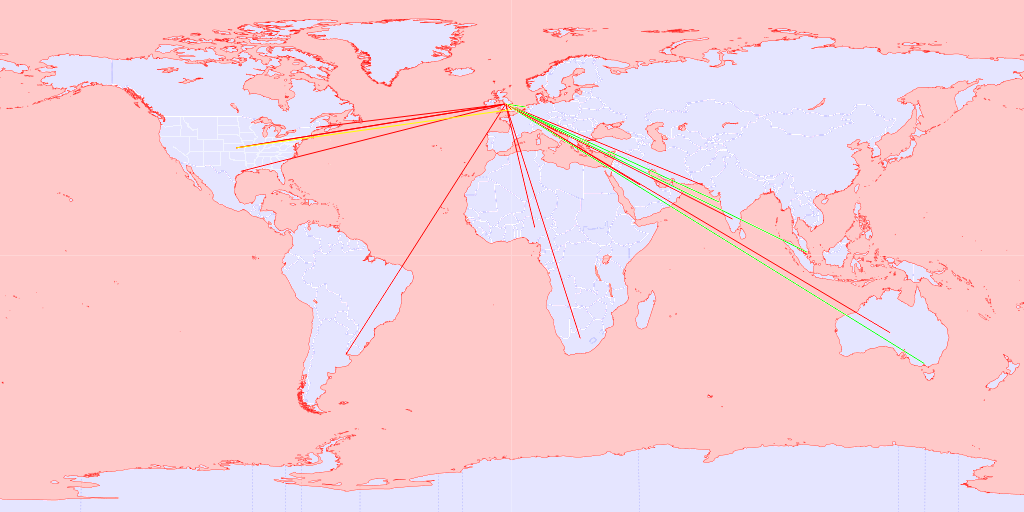
It shows all the connections to their worldwide customers and the activity realtime.
Here you can see the green outbound traffic and red the inbound to their north England location.
Also yellow is showing an unexpected connection from the US to a London location which could be a security problem.
That would have resulted in an email to a company contact to inspect the connection.
Competitor solutions require decryption keys to track data and need to understand the protocol used to track packets.
Requiring decryption keys usually needs purchasing premium accounts and specialist support, MONI does not require this and tracks more intimately.
MONI NetWave uses packet signatures to track packets so can analyse all packets regardless of protocol or packet data.
MONI tracks packets through firewalls and into clients networks regardless of the systems used since it tracks packet payloads.
MONI NetWave uses artificial intelligence and heuristics to tracks packets the same way a good engineer would,
but, unlike even the most expert engineer, MONI can do this real-time for every packet 24 hours a day every day.
This means NetWave understands all traffic not just the known protocols so can spot and analyse things like security risks.

